


Our Company
Over 20+ Years Helping Companies with Technolgy Needs
Most small companies started with a single computer then grew to a dozen or more. As the complexity grew so did the management. We take the headache out of that complexity with State of the Art management tools and techniques
- Experts Problem Solvers
- Insight into your Systems
- Regular Updates & Bug fixes
- High-Rated Quick Remote Support
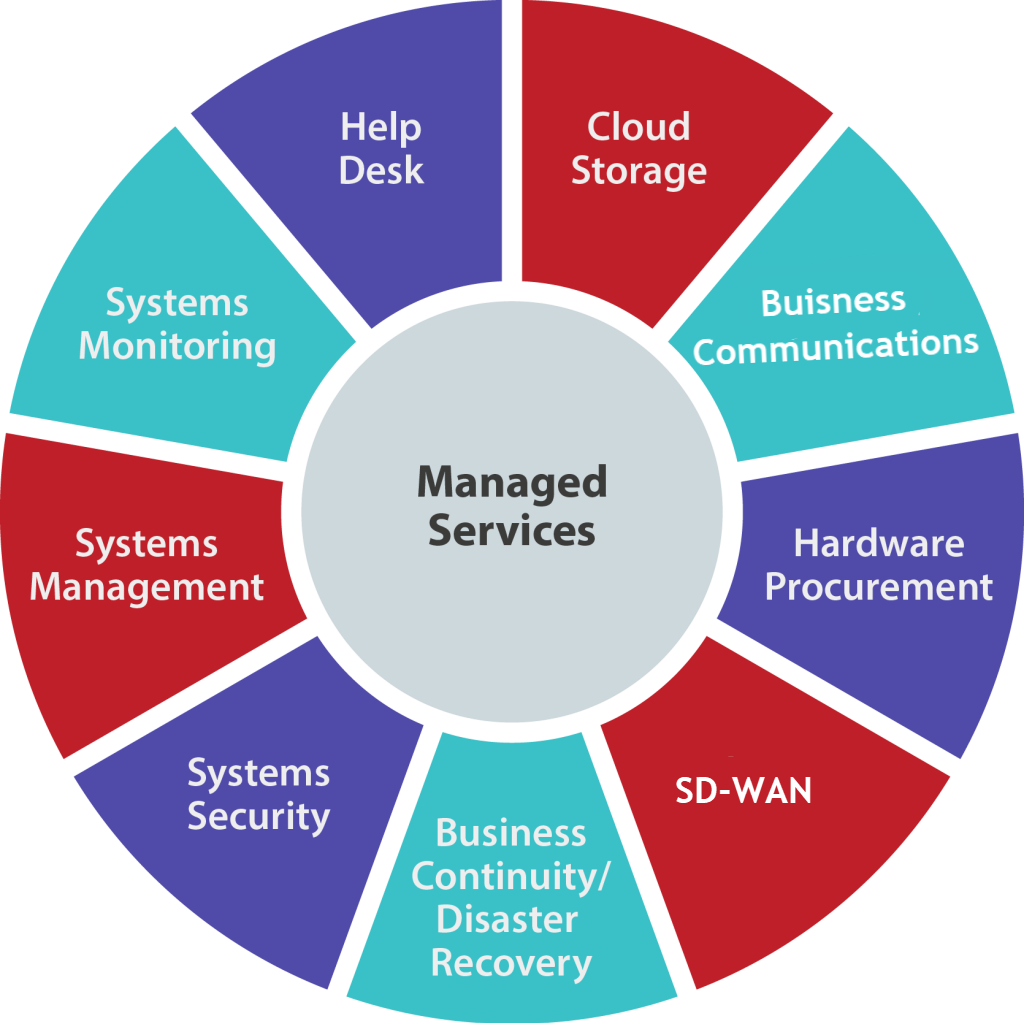
What we do
We Offer Many Types of IT
Solutions Services
We would love to help you
We here to help you 24/7 with experts
With a couple of computers a server isn't necessary but as your network grows a server helps to orchestrate the management, control & security of users & applications.
Cloud computing offers a number of advantages and at the same time creates more risk. It may offer some cost savings initially but in the long run cost more. A thorough analysis of your cost benefits will help to decide which way to go.
PCI DSS compliance although not a law, if not maintained properly can jeopardize your ability to accept cards for payment. Proper compliance starts with a written formal Security Policy. It is important that the policy is kept up to date.
Hackers look for easy targets. Keeping you computers up to date with the latest patches and using strong passwords along with two factor authentication can reduce your vulnerability exposure are a good start towards becoming secure.
75
Happy Customers
500
Project Done
10000s
Support Request
10000s
Support Request Resolved
Post from our Network Operations Center

InterNetwork Service
InterNetwork Service is exactly that. A boutique IT service provider for network planning, installation and maintenance. Basically if it connects to a network then it's in our domain. We are as equally comfortable with OS X as we are with Windows
Warning: opendir(/hermes/walnacweb03/walnacweb03ag/b828/internetworkservice/wp_site_1644255527/wp-content/cache/db/options/): failed to open dir: No such file or directory in /hermes/walnacweb03/walnacweb03ag/b828/internetworkservice/wp_site_1644255527/wp-content/plugins/w3-total-cache/Util_File.php on line 158
Protect Your Smartphone from Hackers – Stay One Step Ahead!
In today’s digital world, safeguarding your smartphone is no longer optional—it’s essential. Hackers can exploit vulnerabilities in your device to access sensitive data, leaving you exposed.
Signs Your Phone May Be Hacked:
📉 Rapid Battery Drain: Unexpectedly fast depletion of battery life.
🚨 Unfamiliar Apps: Apps you don’t remember downloading.
📊 Increased Data Usage: Spikes in your mobile data consumption.
🛑 Frequent Pop-ups: Intrusive or inappropriate ads.
🔄 App or System Crashes: Apps malfunctioning or random restarts.
Steps to Secure Your Device:
1. 🚫 Remove suspicious apps immediately.
2. 🔍 Run antivirus scans with trusted software.
3. 📲 Keep your device and apps updated.
4. 🔒 Avoid public Wi-Fi; use a secure VPN instead.
5. ⚠️ Be cautious with unknown links or downloads.
6. 🕵️♀️ Monitor your accounts for unusual activity.
Take Control with InterNetwork Service
InterNetwork Service offers secure mobile technology to prevent mobile device takeovers. Our advanced solutions shield your phone from hackers, ensuring your personal and professional data remains safe.
Stay proactive, stay secure. Reach out to InterNetwork Service to learn how we can help you protect your devices and data.
#Cybersecurity #MobileSecurity #InterNetworkService #SecureTechnology
... See MoreSee Less

- likes 0
- Shares: 0
- Comments: 0
0 CommentsComment on Facebook
Cybercriminals are increasingly exploiting fake CAPTCHA verification pages to distribute malware, notably the Lumma Stealer, which targets Windows users.
These deceptive pages mimic legitimate human verification systems, such as Google's CAPTCHA, to trick users into executing malicious scripts.
How the Scam Works:
1. Redirection to Fake CAPTCHA Pages: Users are lured through phishing emails or malicious links, often disguised as cracked software downloads or security alerts.
2. Execution of Malicious Scripts: Clicking the "I am not a robot" button on these fake pages copies a malicious PowerShell script to the user's clipboard. Users are then instructed to paste and execute this script, unknowingly initiating the malware installation.
3. Deployment of Lumma Stealer: The script downloads and installs the Lumma Stealer malware, which harvests sensitive information, including login credentials and financial data, from the infected system.
Protective Measures:
Avoid Downloading Cracked Software: Refrain from downloading pirated software, as it is a common vector for malware distribution.
Be Skeptical of Unexpected Verification Pages: Legitimate CAPTCHA pages will not prompt you to download files or execute commands.
Do Not Execute Unknown Scripts: Never copy and run scripts from untrusted sources, especially those that prompt you to use system utilities like PowerShell.
Maintain Updated Security Software: Ensure your antivirus and anti-malware programs are up to date to detect and block such threats.
By staying vigilant and following these precautions, you can protect yourself from falling victim to these sophisticated malware distribution tactics.
... See MoreSee Less

6 CommentsComment on Facebook
Another one Bytes the Dust.
... See MoreSee Less
0 CommentsComment on Facebook









